n
anonymousdoortablet/dthelp.nsfRFID
Protected content
| 248pages | Our help system contains many pages and videos for you to consume. This includes the complete information on how Door Tablet works, all its features and options, and of course the many benefits for your business. Door Tablet School offers many videos too. |
|
 |
| 
Click on images to see them in full screen
4F23D1041F90FFAB80257FCB00336A7EIntroduction to RFID
From Door Tablet V7.7 users of the Door Tablet AIO can exploit its built-in RFID hardware. RFID or NFC (Near Field Communication) allows users to easily identify themselves to Door Tablet and perform a range of functions fast and easily. Using RFID greatly improves security and opens the possibility of new features in the product.
RFID services are currently available on the Door Tablet AIO only. This may change in the future.
How is RFID used
- Users are given low cost RFID tags
- Tags are then used to touch the Door Tablet AIO and the code in the tag is read
- RFID codes are matched with the Door Tablet database on the server and converted to a verified identity
- The above identity is then used in conjunction with various actions
RFID enhanced functions
With version 7.7 of Door Tablet the following functions are enhanced by RFID:
- Administration login - administrators may register their RFID tag and use it for speedy server login
- User RFID cards registration by administrators - registration of this kind is instantly approved
- User RFID self card registration - available from single room and cluster displays. Approval may be delayed and provided later by an administrator, or instantly approved too
- Meeting space Reservations - RFID adds identity to your tablet based reservations. Once a card is used with a reservation, only that card can be used for extensions and terminations of the meeting
- Check-in and check-out - use the card that was previously used to reserve the meeting space or, for pre booked meetings, notify the originator who has checked in
- Meeting Extension and Terminations - use the RFID card to verify you own the meeting, to extend or terminate
- Assistance requests - your ID information is instantly added to your requests
Note: RFID cards may be disabled using the Admin Interface, if lost or abused.
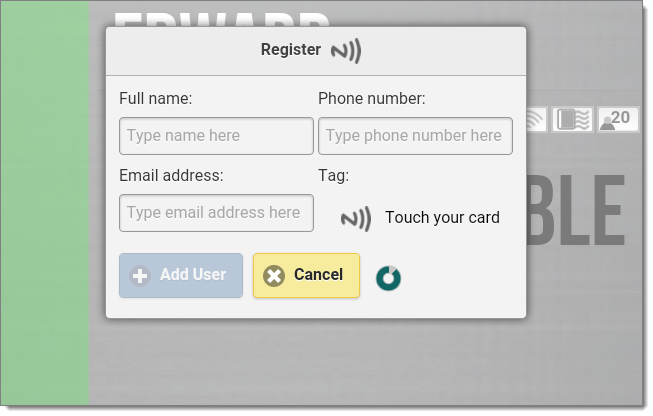
Invitation to touch your RFID card when registering it.
Option 1
 Option 2
When you first import users into Door Tablet. The user has less data to type in, namely they need to provide just the email address. Door Tablet will check the following:
Option 2
When you first import users into Door Tablet. The user has less data to type in, namely they need to provide just the email address. Door Tablet will check the following:
- The RFID code is not already in use
- The user is identified by the email address exists
- There is no RFID code already in the user record
For more details on this option please see 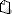
 For the supported RF protocols please see here
For the supported RF protocols please see here 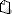 HiD
From version 8.4.18 Door Tablet fully supports HiD cards. Using machines that read HiD is slightly different from standard RFID and is described here
HiD
From version 8.4.18 Door Tablet fully supports HiD cards. Using machines that read HiD is slightly different from standard RFID and is described here 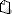 Secure enablement (or option 2a)
As you see above, a user can type an email address in error and if such a user is registered on Door Tablet, the enablement will affect the wrong person. To avoid that, you can ask the system to validate the email address by sending a message to the user, with a number they have to type in. In addition, administrators can specify the domains that will be checked, and restrict the email to only the domains that are listed.
In the system profile, fill in the following fields:
Secure enablement (or option 2a)
As you see above, a user can type an email address in error and if such a user is registered on Door Tablet, the enablement will affect the wrong person. To avoid that, you can ask the system to validate the email address by sending a message to the user, with a number they have to type in. In addition, administrators can specify the domains that will be checked, and restrict the email to only the domains that are listed.
In the system profile, fill in the following fields:
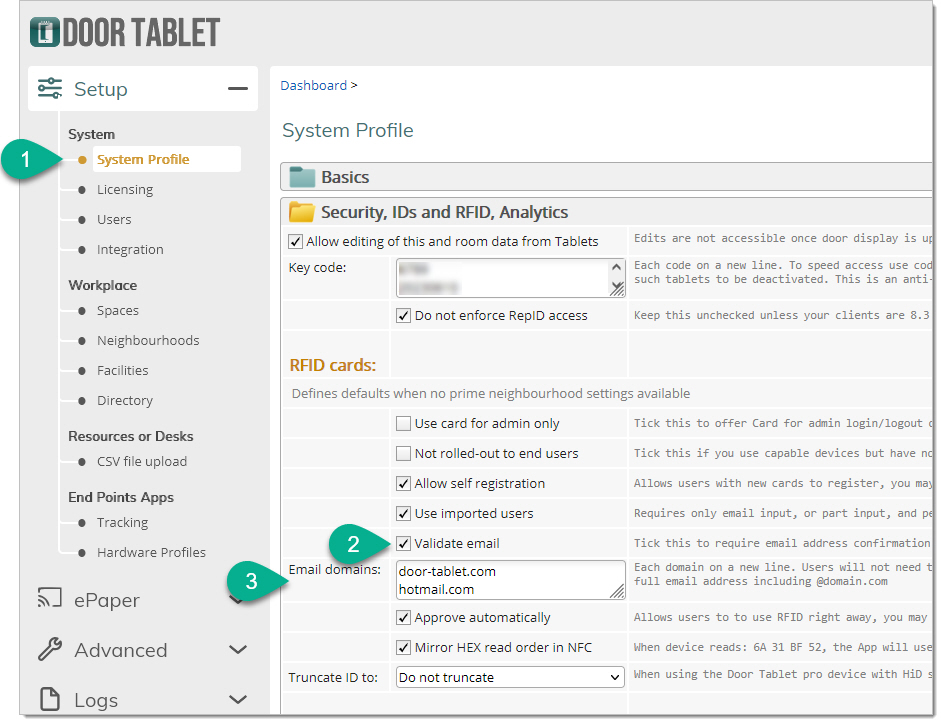 When the user types a valid name, the left part of the email address, and clicks on Reg. RFID, Door Tablet sends an email to the user with the code they need to type in.
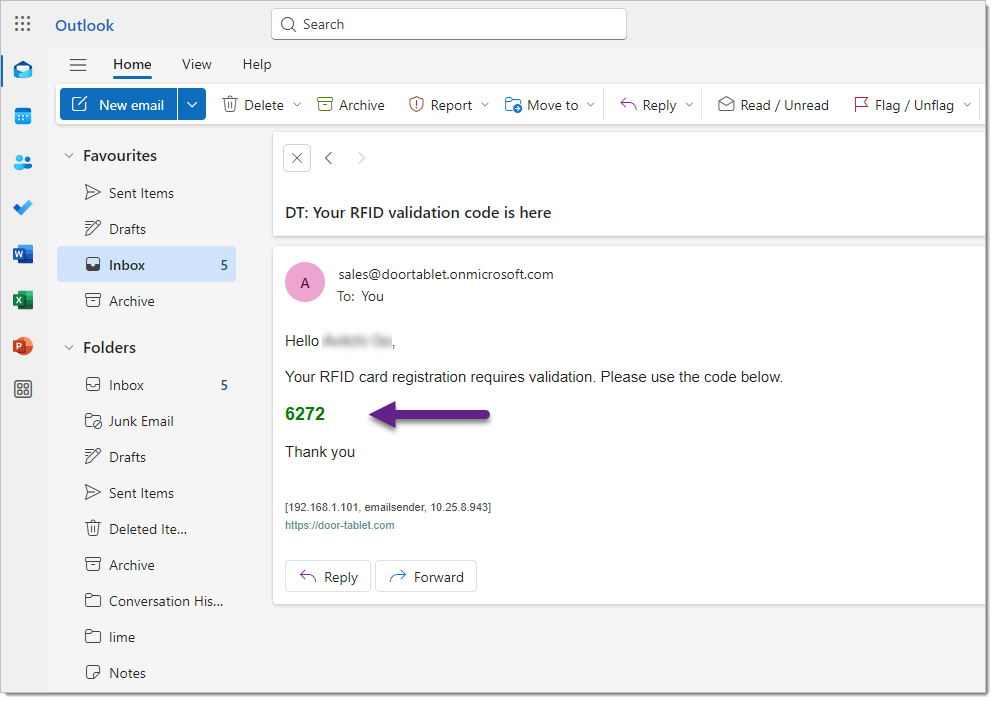
Sample email sent with the validation code:
When the user types a valid name, the left part of the email address, and clicks on Reg. RFID, Door Tablet sends an email to the user with the code they need to type in.
Sample email sent with the validation code:
 The user presents their card...
The user presents their card...
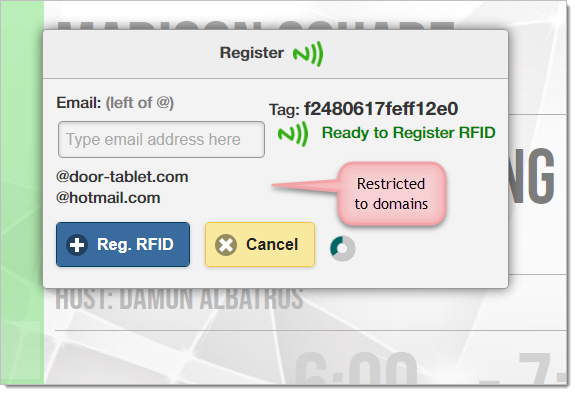 And the tablet shows the field to enter the code...
And the tablet shows the field to enter the code...
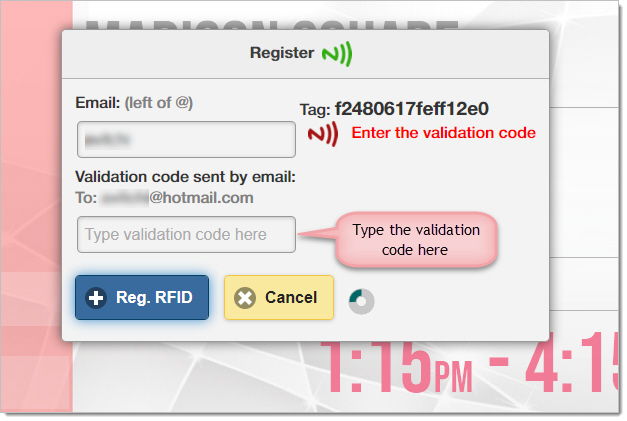 The user clicks on Reg. RFID again to complete the process.
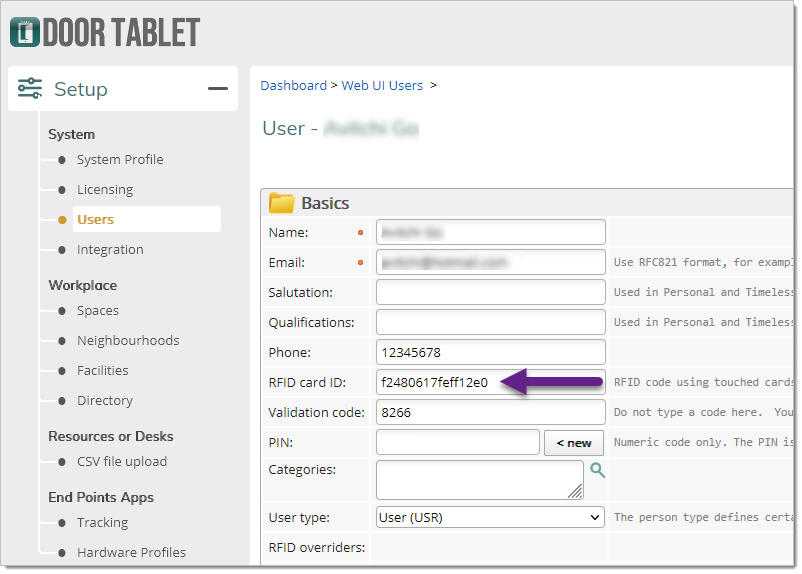
The user record will now show the Tag, as expected:
The user clicks on Reg. RFID again to complete the process.
The user record will now show the Tag, as expected: